Traffic flow within NSX
Below article details the traffic flow that happens within NSX
Host preparation process during NSX installation creates the VXLAN (netcpa) and firewall (vsfwd) capabilities within every host or cluster. Thus every host gets ready to operate NSX attributes.
Transport Zone are considered as the boundary of the VXLANs or the logical switches. Whenever a logical switch is created it is attached to a Transport Zone (Global or Universal).
Since the hosts or the clusters are VXLAN ready thus they communicate with NSX Controllers through User World Agent (UWA) process that operates via netcpa services.
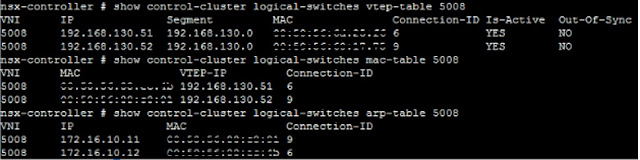
NSX Controllers are privotal in NSX architecture and are part of control plane of NSX architecture as they build and retain VTEP table, MAC table and ARP table for every VNI or VXLAN. In case any host that is not having any of these information first contacts NSX Controllers to gain respective destination MAC/IP details.
NSX Controllers on the other hand build these tables (VTEP table, MAC table and ARP table) after it receives the notification (VM IP Updates) from hosts.
The below snapshot shares the output from the 3 tables with their corresponding commands. Here VXLAN or VNI is 5008.
Checking the check box on Enable IP discovery enables ARP suppression (by forwarding ARP requests to VSX Controllers)
Scenario 1: VM1(MAC1) on Host 1 to reach VM2(MAC2) on Host 2. NSX Controller aware of MAC1 and MAC2
When VM1 on one host tries to ping/reach VM2 on another host and is not aware of the MAC address of VM2. It issues the ARP request towards Host 1. Host 1 sends the request to NSX Controller via UWA. NSX Controller responds back to the Host 1 with the MAC of VM 2 since it is aware of the MAC of VM2 and its corresponding Hosts.
Host 1 now responds back to the ARP requests generated by VM1. Source MAC of the response is that of VM2 i.e MAC2 (thereby making it invisible for VM1)
VM1 is now reachable to VM2.
Scenario 2: VM1(MAC1) on Host 1 tried to reach VM2(MAC2) on Host 2. NSX Controller not aware of MAC1 and MAC2.
When VM1 on one host tries to ping/reach VM2 on another host and is not aware of the MAC address of VM2. It issues the ARP request towards Host 1. Host 1 sends the request to NSX Controller via UWA. Now since NSX Controller is unaware of the MAC of VM2 (MAC2) it responds back to Host1 that it is unaware of the MAC of VM2. This is followed by ARP requests on that VXLAN segment based on the replication mode selected and the requisite hosts respond to the ARP request.
VM1 is now reachable to VM2.
The below snapshot is taken when the ping between 2 VMs with IP address 172.16.10.11 and 172.16.10.12 residing on hosts 192.168.130.52 and 192.168.130.51 respectfully is successful.
It is also of interest to understand that when a VM connects to a logical switch it connects via 3 slot ids each representing a service.
Slot 1 depicts the Switch security module. It captures the DHCP Ack msgs and ARP msgs and then forwards it to NSX Controllers. Any ARP requests are captured by the swsec and is forwarded to NSX Controller. NSX Controller responds back by providing the MAC if it has else send the don't know message.
Meanwhile through VM IP update own VM's MAC address is also sent to NSX Controller.
The below figure captures the details on these vnic slots alongside its respective commands.
Out out of summarize-dvfilter command on ESXi host.
 Below output depicting VTEPs, MACs and ARP request is taken from the ESXi host on the VXLAN of 5008.
Below output depicting VTEPs, MACs and ARP request is taken from the ESXi host on the VXLAN of 5008.Hope you enjoyed reading !







Comments
Post a Comment