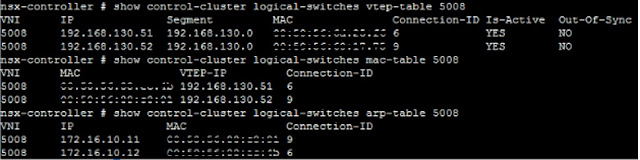
AWS Transit Gateways
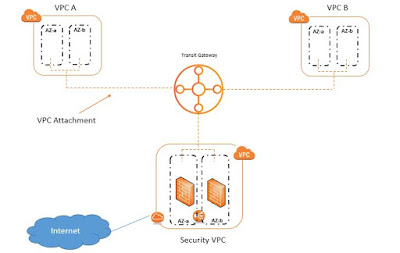
Transit Gateways are a new introduction within AWS architecture to connect different VPCs together to achieve a more controlled routing behavior. This was earlier being achieved by Transit VPC AWS architecture. Transit gateway is a regional object and can be understood as a centralized router to which different VPCs connect. AWS IAM can be used to allow access to users to a Transit Gateway. Presently at the time of writing this article, Maximum of 5000 Attachments are supported per Transit Gateway. Maximum of 5 Transit Gateway attachments are supported per VPC Following components are required to establish a Transit Gateway: ASN (Autonomous System Number) This is required to ensure routing between different AS number. Transit Gateway Attachments There are different ways to connect a VPC or an On-Premise devices to a Transit Gateway. These are called Attachments. There are 2 types of attachments: VPC Attachment VPCs can be attach...